Digital fingerprints on Red October spyware point to Russia ... or do they?
In one of the largest cyberespionage networks ever uncovered, cyberspies operating through a global web of computer servers have over five years siphoned libraries' worth of diplomatic and proprietary data, sensitive documents, e-mails, and passwords from hundreds of government and industry sites worldwide.
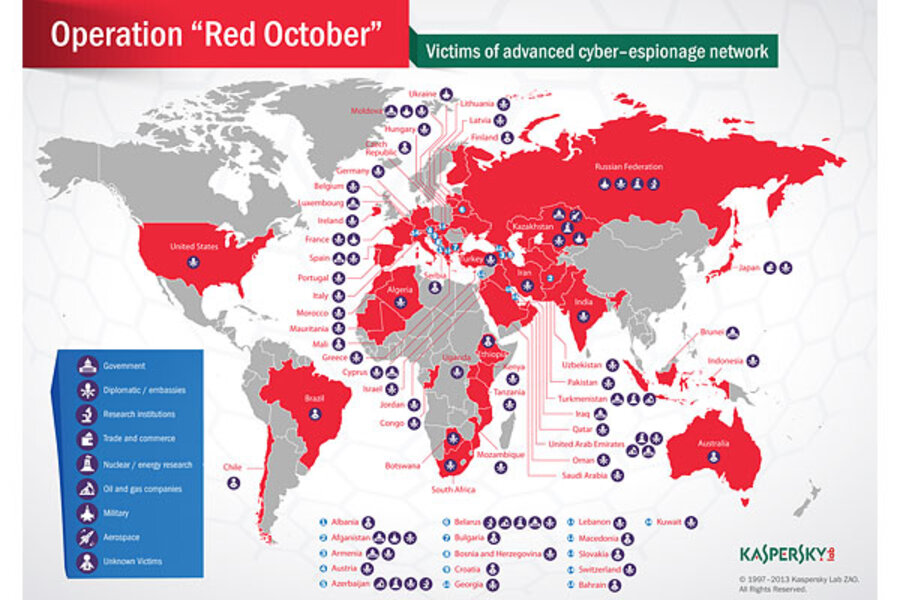
Dubbed Red October, the cyberspy campaign began in 2007, targeting networks inside embassies and research institutes, trade and commerce offices, and energy, aerospace, and defense firms in more than 20 countries. Most targets were in Eastern Europe, but some were in North America and Western European, according to Kaspersky, the Moscow-based cybersecurity firm that unveiled Red October this week.
Besides vacuuming up data and stealing electronic files, the Red October spyware is a utility-knife-style malware that can also infiltrate smartphones, networking equipment, and removable hard drives. After stealing data, it then wipes away any trace it has ever been on those devices.
Even so, tidbits found inside the malicious software code led Kaspersky researchers to reach a startling conclusion: The cyberspies, whoever they are, have a strong connection with their motherland.
"We strongly believe that the attackers have Russian-speaking origins," the company's report concludes. "We've counted several hundreds of infections worldwide – all of them in top locations such as government networks and diplomatic institutions. The infections we've identified are distributed mostly in Eastern Europe, but there are also reports coming from North America and Western European countries such as Switzerland or Luxembourg."
First on the list with the most infections is Russia, where the Red October malware has been detected on 35 systems. Next come Kazakhstan, Azerbaijan, and on down to 11th-place United States, with six infections, Kaspersky reported. Some others, including Canada, Britain, and China, had no infections listed.
With the malware's digital signatures revealed, updated antivirus software has now made Red October largely ineffective. But at its height the espionage web was extraordinarily complex. Attackers created more than 60 domain names linked to dozens of server computers located mostly in Germany and Russia. That chain of servers served as "proxies" to hide the locations of the mini-mothership servers and, finally, a central "mothership" server.
"The ... infrastructure is actually a chain of servers working as proxies and hiding the location of the true 'mothership' command and control server," the report said.
For complexity, the Red October cyberspy network is on par with recent cyberespionage campaigns involving Flame malware, said Igor Soumenkov, a malware expert with Kaspersky Labs, in an interview with the Monitor's Fred Weir. The Flame spyware was detected in Iran, Sudan, Israel, Syria, Saudi Arabia, Lebanon, and Egypt last year. Flame, however, has been linked by Kaspersky and Symantec to the Stuxnet cyberweapon directed to attack Iran's nuclear centrifuge complex in 2009.
Even so, Red October "can hardly be referred to as state-sponsored. It is unknown whether the collected data was used by attackers themselves, or was sold to other interested parties," Mr. Soumenkov said.
Technical obfuscation crafted by Red October's creators kept Kaspersky researchers from reaching the "mothership" and determining who was behind the malware.
Many other uncertainties remain about Red October, and one question concerns which institutions and embassies were actually targeted. The Kaspersky data show that a foreign embassy in the US was infected. But which one? And do all those infections in Russia imply that Russian government institutions were victimized, or rather foreign institutions operating inside Russia?
Kaspersky officials say their investigation is ongoing and won't release target names, something that may give many clues about the identity of the perpetrator. The company says an anonymous source tipped it off to the spy network's existence.
Despite this, Red October reminds some experts of a previous cyberespionage program. That one, GhOstNet, crossed continents and scores of organizations and was found to have a common focal point: Tibet-Chinese relations, Canadian researchers found in 2009. Those researchers, after tracing the IP addresses of servers to China, could not be certain whether the Chinese government or other cyberespionage groups inside China were behind the GhOstNet spying program.
Kaspersky's report identifies a Russian software language set used to create the core Red October spyware program, but it also notes that other "exploit" programs associated with the China-based GhOstNet attack were used, too.
Those exploits "were created by other attackers and employed during different cyber attacks against Tibetan activists as well as military and energy sector targets in Asia," Kaspersky's report says. "The only thing that was changed is the executable which was embedded in the document; the attackers replaced it with their own code."
Still, "there is no evidence linking this with a nation-state sponsored attack," Kaspersky's report concludes, implying cybercriminals may be behind Red October.
US experts who have reviewed the Kaspersky report are divided over who might be behind the malware – a crafty Russian crime syndicate harvesting sensitive information and selling it or holding it for ransom, or a sophisticated nation state, such as China, that devised the malware to make it appear to be Russian.
Either way, the duration and scope of the Red October campaign suggest an "Advanced Persistent Threat," or APT – a term that has become shorthand in recent years for years'-long, 24/7, Chinese cyberspying activities.
China is always a suspect in such cases, cyberespionage experts say. In this one, China is one of the few countries with no Red October infections. Of course, Canada and Britain don't either.
"The most interesting thing about Red October, in my opinion, is that it looks a lot like the Chinese pretending to be Russian," says David Aitel, CEO of Immunity Inc., a Miami-based cybersecurity company. "The one major country not targeted is China. If this was a Russian team, you're not going to target Uganda before you target China. It was a really good job of pretending to be Russian. But the targets never lie; the one thing they can't hide is what they're targeting."
But to John Bumgarner, research director for the US Cyber Consequences Unit, a nonprofit group that studies cyberthreats, the Kaspersky report is more than suggestive about Russia's cyberactivities.
"This report provides the hard evidence that Russia is a major player in cyberespionage," he says. "The United States and China are the other key players in this cold-war-style game of cyberespionage."
Buried in the Red October spyware is the word "PROGA," which might be a transliteration of slang among Russian-speaking software engineers that literally means an application or a program, Kaspersky reported. Another word, "Zakladka," in Russian can mean "bookmark" or, more likely, is slang for "a microphone embedded in a brick of the embassy building" – the sort of clandestine intelligence-gathering conducted by both Russia and the US in the 1950s and '60s.
One cybersecurity expert, who asked for anonymity because of the sensitivity of his position, says the Kaspersky report's conclusions have teeth.
"This is not the first time we've seen Russia, very recently, becoming a player in the cyberespionage game," he says. "This stuff [the slang in the software] is really very hard to fake."
Any whodunnit is impossible to sole without more information, says Graham Cluley, senior technology consultant at the antivirus firm Sophos, in Oxford, England, in a phone interview. But the findings so far are reminiscent of another period of deliberate obfuscation.
"It is such a tangled web, really a bit like tactics from the cold war," Mr. Cluley says. "Yes, it's possible to analyze a piece of code and see the language setting on the compiler and say, 'Hey, this setting is for Russian and assume it comes from there.'
"But with stakes so high, it's equally possible that someone in Belgium, Canada, or China is just trying to mislead," he adds. "I wouldn't fall off my chair in shock if China was behind it after all."