All Passcode Voices
 Opinion: The case for safeguarding students' digital privacyAccording to a new survey, parents care as much about safeguarding kids' data as they do about their own financial information security. It's time for schools to become better stewards of data while teaching kids to be smarter and safer online.
Opinion: The case for safeguarding students' digital privacyAccording to a new survey, parents care as much about safeguarding kids' data as they do about their own financial information security. It's time for schools to become better stewards of data while teaching kids to be smarter and safer online. Five predictions for cybersecurity's role in the 2016 presidential raceThis election cycle could see cybersecurity play its largest role yet. Recent events such as the hacks of Sony Pictures, Anthem, and the Office of Personnel Management have brought the issue to public attention.
Five predictions for cybersecurity's role in the 2016 presidential raceThis election cycle could see cybersecurity play its largest role yet. Recent events such as the hacks of Sony Pictures, Anthem, and the Office of Personnel Management have brought the issue to public attention. Opinion: Restraint is the best weapon against Chinese hacksWhen Chinese President Xi visits the US this month, President Obama has a rare chance to forge a strategic deal with China to ease the growing cyberconflict between Washington and Beijing.
Opinion: Restraint is the best weapon against Chinese hacksWhen Chinese President Xi visits the US this month, President Obama has a rare chance to forge a strategic deal with China to ease the growing cyberconflict between Washington and Beijing. Opinion: On cybersecurity info sharing, it’s the medium not the messageIf Congress succeeds in pushing through CISA, neither the bill in its current form – nor any of the amendments – will do much to increase the effectiveness or timeliness of cybersecurity information sharing.
Opinion: On cybersecurity info sharing, it’s the medium not the messageIf Congress succeeds in pushing through CISA, neither the bill in its current form – nor any of the amendments – will do much to increase the effectiveness or timeliness of cybersecurity information sharing. Opinion: How digital voyeurism is destroying privacyOur inability to turn away when hackers and digital eavesdroppers publish someone's intimate details online encourages others to do the same, chipping away at everyone's ability to keep secrets.
Opinion: How digital voyeurism is destroying privacyOur inability to turn away when hackers and digital eavesdroppers publish someone's intimate details online encourages others to do the same, chipping away at everyone's ability to keep secrets. Opinion: Why bug hunting security researchers are Digital Age heroesComments from an Oracle executive disparaging the work of security researchers misunderstands their value and ethic. While hackers poking around in code may irritate software companies, their work has made computers safer for everyone.
Opinion: Why bug hunting security researchers are Digital Age heroesComments from an Oracle executive disparaging the work of security researchers misunderstands their value and ethic. While hackers poking around in code may irritate software companies, their work has made computers safer for everyone. Opinion: Twitter's privacy blunderTwitter's decision to give companies instant access to every public post means that users' comments will be tracked, mined, and analyzed more than ever before. Perhaps it's time to think twice before you tweet.
Opinion: Twitter's privacy blunderTwitter's decision to give companies instant access to every public post means that users' comments will be tracked, mined, and analyzed more than ever before. Perhaps it's time to think twice before you tweet. Opinion: Retaliation against China is the wrong reaction to OPM hackEven if Beijing was responsible for breaches that exposed sensitive data on millions of Americans, a diplomatic or economic response only distracts from the US government's most pressing problem: bolstering security measures to foil the next attack.
Opinion: Retaliation against China is the wrong reaction to OPM hackEven if Beijing was responsible for breaches that exposed sensitive data on millions of Americans, a diplomatic or economic response only distracts from the US government's most pressing problem: bolstering security measures to foil the next attack. Opinion: Why the information sharing bill is anti-cybersecuritySupporters of the Cybersecurity Information Sharing Act says it's an essential tool for Washington and industry to exchange threat intelligence. But in reality, it would give the government carte blanche to collect and store more data on Americans, putting everyone's information at greater risk.
Opinion: Why the information sharing bill is anti-cybersecuritySupporters of the Cybersecurity Information Sharing Act says it's an essential tool for Washington and industry to exchange threat intelligence. But in reality, it would give the government carte blanche to collect and store more data on Americans, putting everyone's information at greater risk.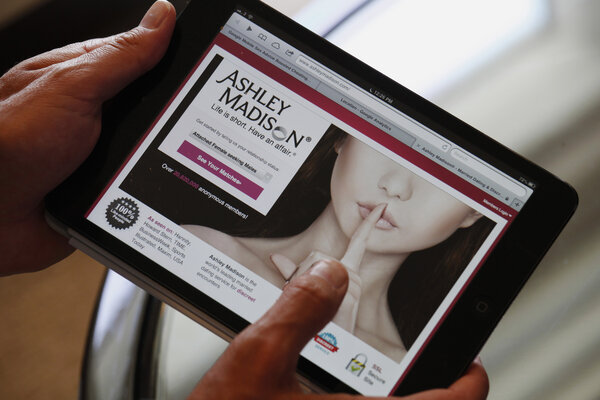 Opinion: Ashley Madison hack reveals need for new approach to guard intimate dataAfter its users' data was exposed online, Ashley Madison issued copyright takedown notices to have it removed. It's a bad use of copyright law but reflects a troubling legal environment where digital media companies own users' most personal images and information.
Opinion: Ashley Madison hack reveals need for new approach to guard intimate dataAfter its users' data was exposed online, Ashley Madison issued copyright takedown notices to have it removed. It's a bad use of copyright law but reflects a troubling legal environment where digital media companies own users' most personal images and information. Opinion: The value of unmasking Tor's dark sideThe identity shrouding Tor browser is a godsend for many people – including criminals – trying to avoid detection online. But using it doesn't erase everyone's digital footprints, giving researchers many clues for hunting down Tor's more nefarious users.
Opinion: The value of unmasking Tor's dark sideThe identity shrouding Tor browser is a godsend for many people – including criminals – trying to avoid detection online. But using it doesn't erase everyone's digital footprints, giving researchers many clues for hunting down Tor's more nefarious users. Opinion: Hacking Team breach a gold mine for criminal hackersWhile the breach at the Italian spyware firm shines a light on the shadowy world of surveillance technology, it has also made the Web a much more dangerous place, giving criminal hackers even more tools to ply their craft.
Opinion: Hacking Team breach a gold mine for criminal hackersWhile the breach at the Italian spyware firm shines a light on the shadowy world of surveillance technology, it has also made the Web a much more dangerous place, giving criminal hackers even more tools to ply their craft. Opinion: Why privacy alarmists are wrong about data rules in big trade dealsProvisions in the Trade in Services Agreement, which is currently under negotiation in Geneva, are not meant to erode privacy. Instead, the pact reflects the reality of how data is stored and transmitted in the modern global digital economy.
Opinion: Why privacy alarmists are wrong about data rules in big trade dealsProvisions in the Trade in Services Agreement, which is currently under negotiation in Geneva, are not meant to erode privacy. Instead, the pact reflects the reality of how data is stored and transmitted in the modern global digital economy. Opinion: Timing is everything for securing wireless communicationsEven though disrupting wireless communications – whether cellphone networks or GPS – could harm the US economy and put lives at risk, these networks remain far too vulnerable to attacks.
Opinion: Timing is everything for securing wireless communicationsEven though disrupting wireless communications – whether cellphone networks or GPS – could harm the US economy and put lives at risk, these networks remain far too vulnerable to attacks. Opinion: An Underwriters Laboratories for cybersecurity is long overdueNoted security researcher Mudge left Google to launch what appears to be the cybersecurity equivalent of electronics testing outfit Underwriters Laboratories – an idea first proposed 16 years ago.
Opinion: An Underwriters Laboratories for cybersecurity is long overdueNoted security researcher Mudge left Google to launch what appears to be the cybersecurity equivalent of electronics testing outfit Underwriters Laboratories – an idea first proposed 16 years ago. Opinion: It's time for an about-face on facial recognitionThe breakdown in talks between advocacy groups and industry over facial recognition guidelines should alarm anyone who doesn't want to be recorded, identified, and cataloged everywhere they go.
Opinion: It's time for an about-face on facial recognitionThe breakdown in talks between advocacy groups and industry over facial recognition guidelines should alarm anyone who doesn't want to be recorded, identified, and cataloged everywhere they go. Opinion: Paper, the least terrible password management toolWith password management app LastPass possibly compromised, a stowed away pad of paper seems more secure than storing sensitive credentials in the cloud.
Opinion: Paper, the least terrible password management toolWith password management app LastPass possibly compromised, a stowed away pad of paper seems more secure than storing sensitive credentials in the cloud. Opinion: #CyberDeflategate and the beginning of sports hackingIt was only a matter of time before American sports added hacking to its tricks for gaining the upper hand. But unlike other cheating scandals that have led to suspensions and fines, computer crimes can lead to prison time.
Opinion: #CyberDeflategate and the beginning of sports hackingIt was only a matter of time before American sports added hacking to its tricks for gaining the upper hand. But unlike other cheating scandals that have led to suspensions and fines, computer crimes can lead to prison time. Opinion: The reasonable expectation fallacyThe ability to delete yourself from the Web doesn't really matter. What really matters in the age of advanced surveillance is the right to not be correlated. Technology is always watching and capturing you, but the correlation is where the danger lies. Laws can change that, but only if enacted soon.
Opinion: The reasonable expectation fallacyThe ability to delete yourself from the Web doesn't really matter. What really matters in the age of advanced surveillance is the right to not be correlated. Technology is always watching and capturing you, but the correlation is where the danger lies. Laws can change that, but only if enacted soon. Opinion: Is Surespot the latest cryptowar victim?The encrypted chat app has been mum since suggesting it was about to receive a government subpoena. Its silence implies that the government may be snooping on its users, which have included Islamic State militants.
Opinion: Is Surespot the latest cryptowar victim?The encrypted chat app has been mum since suggesting it was about to receive a government subpoena. Its silence implies that the government may be snooping on its users, which have included Islamic State militants.























