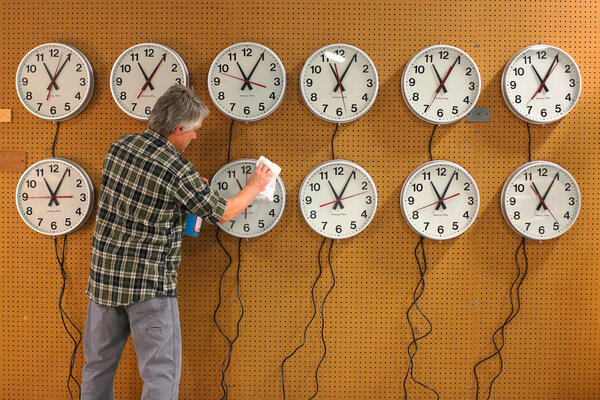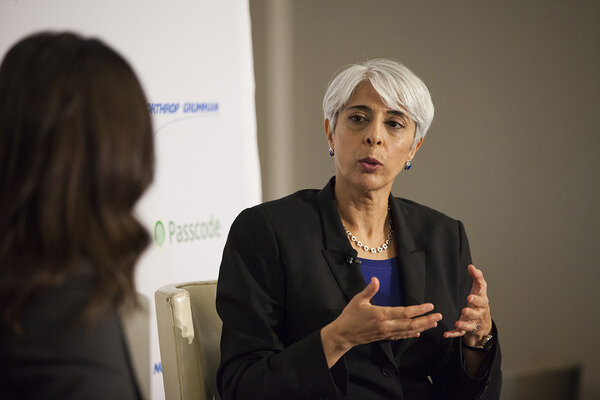All Passcode
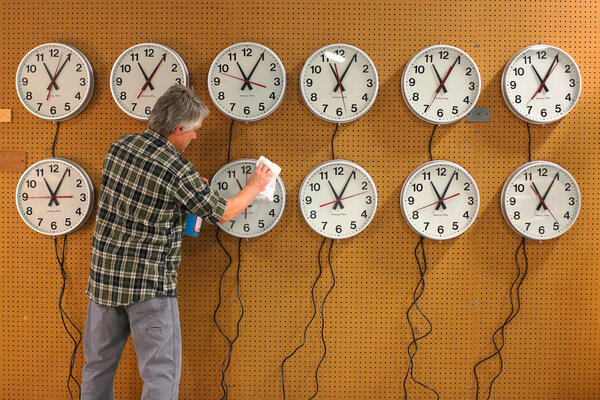 Researchers reveal how attackers could turn back Internet time
Researchers reveal how attackers could turn back Internet timeBoston University researchers discovered vulnerabilities in the ubiquitous computing protocol that keeps time synched across networks, opening up critical operations such as air traffic control to attacks.
 Opinion: Why the 'cyber bill' falls short on protecting critical networks
Opinion: Why the 'cyber bill' falls short on protecting critical networksThe Cybersecurity Information Sharing Act is missing a key component needed to strengthen America's digital defenses – transparency into what the government itself is doing or not doing to protect its networks from hackers.
 What automakers can teach us about securing the Internet of Things
What automakers can teach us about securing the Internet of ThingsWhile 'Back to the Future Part II' didn’t envision connected cars, car companies are working together to safeguard a cornerstone of the Internet of Things
- Watch live: How can policymakers help secure the Internet of Things?
Join Passcode on Oct. 21 along with policy experts and lawmakers for a discussion on one of today's preeminent challenges: securing the Internet of Things.
 Opinion: Advice for Congress, the weakest link in cybersecurity
Opinion: Advice for Congress, the weakest link in cybersecurityAs soon as Congress realizes that good security and privacy practices are paramount to cultivating a thriving tech economy, it can begin working with Silicon Valley to forge a more prosperous digital future.
 Influencers: Revise copyright law so researchers can tinker with car software
Influencers: Revise copyright law so researchers can tinker with car softwareA majority of Passcode Influencers said the US should revise copyright laws so that people can legally tinker with automotive software in light of the Volkswagen scandal.
 Opinion: Why we all have a stake in encryption policy
Opinion: Why we all have a stake in encryption policyRapid advances in technology could soon turn science fiction notions of effortless encryption into a reality. But ensuring that we can trust that technology will take more public vigilance against government and corporate eavesdropping.
 Opinion: Presidential campaigns' thirst for big data threatens voter privacy
Opinion: Presidential campaigns' thirst for big data threatens voter privacyPresidential campaigns are using sophisticated data mining and analytics software to gain the edge when it comes to courting voters. But the wholesale collection, storage, and sale of voters' political information raises serious questions over how potential supporters are targeted and how their information is exploited.
- Watch live: Will the costs of cyber insecurity outweigh connectivity's benefits?
Join Passcode and the Atlantic Council's Brent Scowcroft Center on International Security for a discussion on the Atlantic Council's report "Risk Nexus: Overcome by Cyber Risks? Economic Benefits and Costs of Alternate Cyber Futures" on Oct. 15 from 9 to 10:30 am.
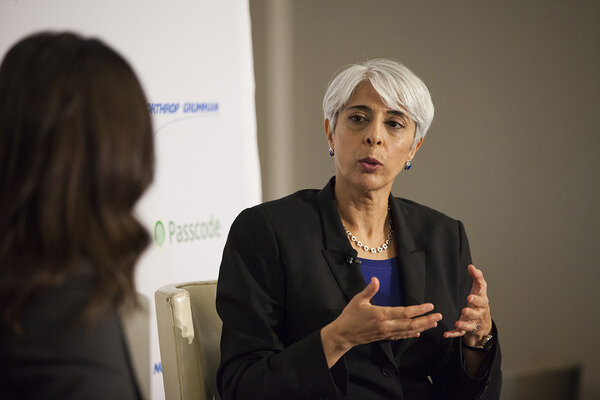 DARPA director on the future of war and securing the Internet of Things
DARPA director on the future of war and securing the Internet of ThingsAt a Passcode event on Thursday, Defense Advanced Research Projects Agency Director Arati Prabhakar, along with leading government figures in cybersecurity, offered a rare glimpse into research happening in government labs.
 EU diplomat: Safe Harbor 2.0 must guard Europeans’ 'fundamental rights'
EU diplomat: Safe Harbor 2.0 must guard Europeans’ 'fundamental rights'In an interview at the Monitor on Thursday, David O’Sullivan, the European Union’s ambassador to the US, said he was confident that Europeans and their American counterparts could forge a new transatlantic data transfer deal that included more robust privacy protections.
- Cyber resilience: Enabling control of the cyber domain
Speed in cyber will be as strategically important to tomorrow's conflicts as stealth, precision guided weapons are today.
 Opinion: With pervasive government surveillance, there are no safe harbors
Opinion: With pervasive government surveillance, there are no safe harborsThis week's European ruling striking down the transatlantic Safe Harbor deal is a stark reminder that no one's data is safe until governments around the world reform digital surveillance practices.
 Opinion: Why the global tech industry needs Safe Harbor 2.0
Opinion: Why the global tech industry needs Safe Harbor 2.0The demise of Safe Harbor may be a victory for privacy advocates but it leaves global tech companies in the lurch. A new version of the deal is needed so that companies can get back to work while improving privacy protections for users around the world.
- In cybersecurity, it's (almost) all about the people
In cybersecurity as in life, hammers don’t drive nails on their own. It’s all about the people behind the tools. Here are the three things enterprises need to do to unleash the power of their analysts.
- Watch live: Managing our nation's cyber risk
Join Columbia University for an in-depth discussion focused on how the US is protecting against cyber threats.
 What the EU Safe Harbor ruling means for data privacy
What the EU Safe Harbor ruling means for data privacyThe Court of Justice of the European Union on Tuesday invalidated a data transfer deal between the US and EU in a move that could have broad repercussions for thousands of American businesses.
- Watch live: The cutting edge of cybersecurity research
How are different government agencies working to address evolving security challenges? Join Passcode on Oct. 8 for a conversation with senior officials to get an inside look at how these challenges are being addressed.
 Opinion: The troubling rise of Internet borders
Opinion: The troubling rise of Internet bordersIf countries erect more borders and limits in the digital domain, the engine of global social and economic change that's powered by the Internet will quickly stall.
 Sensitive student data at risk on top college websites
Sensitive student data at risk on top college websitesEven as universities suffer a growing number of breaches, most school websites lack security protocols that can prevent hackers from stealing students' information.