All Passcode
 State Department Cyber Coordinator: We don’t want a cyberarms treaty
State Department Cyber Coordinator: We don’t want a cyberarms treatyAt a Passcode event on Thursday, State Department Cyber Coordinator Chris Painter said the US is still grappling with basic definitions in the digital realm – such as, what constitutes a cyberweapon – complicating the idea of a formal accord to control their use.
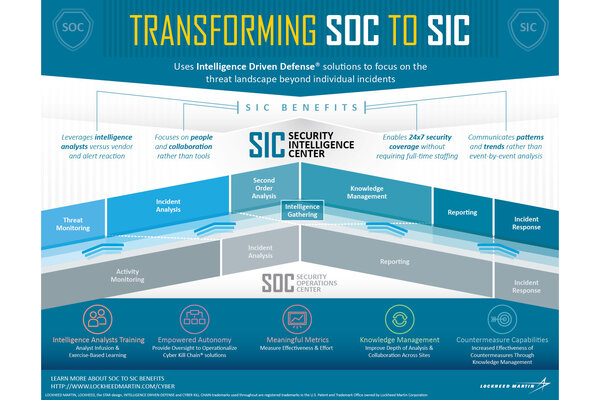 Introduce intelligence to your security operations
Introduce intelligence to your security operationsLockheed Martin is working to address cybersecurity threats by developing more robust security centers.
 Opinion: Why Microsoft's data access case matters to everyone on the Internet
Opinion: Why Microsoft's data access case matters to everyone on the InternetThe ongoing legal dispute between Microsoft and the US government over access to information held in Irish data servers is about more than the company's European business. It's about whether users everywhere can ever trust that their information is safe on the Web.
 Watch live: The future of America's cyber strategy
Watch live: The future of America's cyber strategyJoin Passcode for a conversation with senior policymakers – including the State Department Cybersecurity Coordinator Chris Painter and Deputy Assistant Secretary of Defense for Cyber Policy Aaron Hughes – to discuss America's emerging strategy in cyberspace.
 How one university is approaching the 'wicked problem' of cybersecurity
How one university is approaching the 'wicked problem' of cybersecurityArizona State University launches the Center for Cybersecurity and Digital Forensics with a multidisciplinary approach to cyber’s biggest challenges.
 Researcher: Enemies at Mac's Gatekeeper have way around OS X security measure
Researcher: Enemies at Mac's Gatekeeper have way around OS X security measureApple was plagued by trojan-type malware until it launched Gatekeeper in 2012. It seemed to stem the tide. But new research from the firm Synack shows that it’s relatively simple to skirt Gatekeeper.
 European Parliament member presses to change spyware export rules
European Parliament member presses to change spyware export rulesAs the European Union invites comments on many of its export regulations, Dutch Member of European Parliament Marietje Schaake wants to change surveillance software trading rules many critics say are too onerous. But some security experts say those changes do not go far enough.
 Opinion: Fight phishing without blaming victims
Opinion: Fight phishing without blaming victimsCriminal hackers are skilled at crafting fake e-mails that dupe recipients. But instead of blaming the employees who click links that infect computers, organizations should work harder to fortify their networks.
 Influencers: Lawsuits to prevent reporting vulnerabilities will chill research
Influencers: Lawsuits to prevent reporting vulnerabilities will chill researchCompanies pursuing legal action against security researchers to prevent them from revealing the vulnerabilities they find discourages further critical research, said a majority of Passcode's Influencers.
 What does it mean to take a full-spectrum approach to cybersecurity?
What does it mean to take a full-spectrum approach to cybersecurity?How a full-spectrum approach including defensive cyber, active defense and cyber resiliency keeps America ahead of digital threats.
 Podcast: Congressman Hurd on why it's 'outrageous' OPM never apologized
Podcast: Congressman Hurd on why it's 'outrageous' OPM never apologizedCybersecurity pro and undercover CIA officer-turned-Republican Rep. Will Hurd, and Chris Valasek of recent car-hacking fame, join New America’s Peter Singer and Passcode’s Sara Sorcher on The Cybersecurity Podcast.
 Opinion: Even if flawed, cybertheft deal with China a win for Obama
Opinion: Even if flawed, cybertheft deal with China a win for ObamaWhile President Xi Jinping's public rejection of cyberattacks for commercial espionage has been widely panned, the deal between Washington and Beijing gives the US a much stronger hand to confront China over its actions in the digital realm.
 Chinese activists in US blame Beijing for relentless cyberattacks
Chinese activists in US blame Beijing for relentless cyberattacksWhile criticism aimed at President Xi during his state visit has focused on China's suspected cyberattacks on US agencies and businesses, activists also say they are under constant digital assault from the Chinese government.
 Will $1 million iOS bug bounty compel Apple to pay for software flaws?
Will $1 million iOS bug bounty compel Apple to pay for software flaws?Zerodium, a firm that counts spy agencies as customers, has offered to pay $1 million for information about holes in Apple’s mobile operating system, alarming civil liberties advocates and highlighting Apple’s unwillingness to pay researchers for similar work.
 NSA chief admits risk in decrypting smartphone data
NSA chief admits risk in decrypting smartphone dataAdm. Mike Rogers has long posited that strong encryption on consumer devices hampers law enforcement and intelligence work. But on Thursday he acknowledged the possible security downside of one proposed way for the government to decrypt data on consumer devices.
 'Hackers' at 20
'Hackers' at 20How a 20-year-old, mostly inaccurate flop predicted the future, reshaped sci-fi, and won over the real hacker community.
 Why secure e-mail startup Lavaboom imploded
Why secure e-mail startup Lavaboom implodedAfter encrypted webmail service Lavabit closed under FBI pressure to reveal data about users – Edward Snowden reportedly among them – Lavaboom launched to take up the mantle. But about a year after launching, it has collapsed amid legal and financial woes.
 Why secure e-mail startup Lavaboom imploded
Why secure e-mail startup Lavaboom implodedAfter encrypted webmail service Lavabit closed under FBI pressure to reveal data about users – Edward Snowden reportedly among them – Lavaboom launched to take up the mantle. But about a year after launching, it has collapsed amid legal and financial woes.
 Opinion: It's time the world stood up for the whistleblowers
Opinion: It's time the world stood up for the whistleblowersFrom Daniel Ellsberg to Edward Snowden, Whistleblowers play a key role in bringing greater transparency to government, giving people the ability to scrutinize the actions of their officials and elected leaders. We should all do more to protect them.
 How obsessive self-tracking is eroding privacy for everyone
How obsessive self-tracking is eroding privacy for everyoneSociologist Deborah Lupton says the growing use of health tracking technology is conditioning society to reveal more personal information about themselves, often giving it to corporations interested only in turning a profit.





















