Influencers: US should hit Russia harder for political hacks
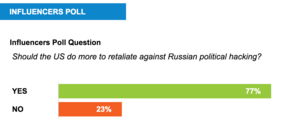
The US should retaliate more strongly against Russia for its digital attacks on American political organizations, more than three-quarters of Passcode’s Influencers said.

Illustration by Jake Turcotte
The US should retaliate more strongly against Russia for its digital attacks on American political organizations, more than three-quarters of Passcode’s Influencers said.
Earlier this month, the US intelligence community released a report that blamed President Vladimir Putin for ordering a campaign of cyberattacks, propaganda, and fake news to undermine public confidence in the democratic process and discredit Hillary Clinton’s campaign.
In light of this, Passcode’s group of digital security and privacy experts said President Trump should roundly condemn the hacks – and impose serious consequences.
“If the Russians had physically sent agents into the offices of the Democratic National Committee to steal files or into polling stations to stuff ballot boxes, they would have done so certain of consequences if those agents were caught: they’d be imprisoned and probably tried,” said Nate Fick, chief executive officer of Endgame, a cybersecurity company. “Until the US government makes explicitly clear that the full weight of American power is available to respond to hostile cyber adventurism, we can expect the assaults on our institutions to continue.”
The Obama administration’s response included economic sanctions, the expulsion of 35 diplomats, the designation of voting systems as critical infrastructure, and strong hints of covert retaliation. Yet some members of Congress criticized Mr. Obama’s response to the hacks – coming six months after suspected Russian breaches into the Democratic National Committee were detected – as too slow.
It’s not yet clear how Mr. Trump plans to deal with the issue.
The new commander-in-chief has said he agrees with the intelligence community’s united assessment that Moscow was behind the suspected digital attacks and leaking of confidential emails to the antisecrecy site WikiLeaks, but has so far declined to publicly condemn Russia for its actions. Some Trump advisers have suggested the post-hack sanctions may even have gone too far – though some of Trump’s cabinet choices, such as CIA Director Mike Pompeo and Defense Secretary James Mattis, have taken a harder line.
Some Influencers are worried that Trump might not act – and are calling on Congress to step in. “Congress should pass bipartisan sanctions against Russia to inflict additional costs and prevent those costs from being easily reversed by the Trump administration,” said Chris Finan, chief executive officer of Manifold Technology.
Peter Singer, a senior fellow at New America think tank, sees the next phase as a test for the Republican-controlled government. “The Obama administration’s recent moves to sanction Russia for targeting US democracy were a good start, albeit too little and too late — criticism that the Republican congressional leadership was quick, and right, to make,” Mr. Singer says. “A test of its sincerity will be whether Congress backs its words with action, by turning the sanctions into law and strengthening them further.”
For his part, Congressional Cybersecurity Caucus cochair Rep. Jim Langevin (D) of Rhode Island says he supported the Obama administration’s actions – but will advocate in the legislative branch for more action. “I do believe that the actions made public to date are not commensurate with the enormity of the attack on the fundamental underpinnings of our democracy,” Mr. Langevin said. “I will continue to support efforts by the Congress and the new Administration to ensure that Russia does not again threaten our electoral systems.”
The US has a variety of tools besides sanctions at its disposal. One Influencer is calling for a “tit-for-tat” response. “There should be a price for their actions, and it should involve doxing powerful Russians connected to the Kremlin so they get the point,” said the expert, calling for a kind of cyberattack ultimately aimed at exposing sensitive information. (Passcode’s Influencers can choose to keep their responses anonymous to preserve their candor.)
A lack of a strong public response will only encourage “bolder behavior” from Russia, added Eric Burger, a computer science professor and director of the Center for Secure Communications at Georgetown University. The US arsenal ranges “from hacking back and exposing Botox use all the way through kinetic warfare, with things like sanctions, public shaming, and the like in between,” he adds.
The probe into suspected Russian digital interference into US elections isn’t over yet: The House and Senate Intelligence committees are investigating the hack.
Even so, Passcode’s experts largely believe that by taking a strong stand now, the US can play an important role in creating rules of the road for cyberspace – or internationally accepted norms of behavior. That process has moved slowly in international bodies such as the United Nations, but experts say a public response to the high-profile hacks could spur some momentum.
“Let’s call it what it is: a digital attack on one a foundational element of societal confidence,” said Steve Weber, a professor at the School of Information at the University of California at Berkeley of this summer’s cyberattacks against the DNC and other Democratic political organizations.
“Now is the time to set some norms about how states use the internet to create corrosion in the social contract of other states. We shouldn’t wait for norms to ‘evolve’ – we should state clearly what we consider out-of-bounds behaviors, not engage in them ourselves, and punish those who do with serious costs and pain.”
However, some experts insist it’s too early to begin talking about further penalties for the suspected Russian digital attacks. A small but vocal 24 percent minority of Influencers said it wasn’t the right time to respond, given a lack of what they said was compelling evidence.
“Until we actually see the evidence of Russian political hacking, this entire episode remains unverified.” says Sascha Meinrath, who heads up X-Lab, a Washington-based venture focused on technology policy and innovation. “Anyone promoting retaliation is doing so in ignorance.” While the intelligence community’s declassified report on Russian hacks featured some technical indicators, such as internet protocol addresses, the public evidence did little to satisfy some security researchers.
Some of Passcode’s experts think that by retaliating more strongly – or mounting a digital counterattack against Russia – the US could make itself vulnerable by exposing its own digital espionage operations to potential criticism.
“Offensive operations are a critical part of nation-state intelligence,” says Nick Selby, from US cybersecurity firm Secure Ideas. “Feigning outrage at operations results in embarrassing propaganda campaigns in which we must ‘demonstrate’ how awful it all is.”
The US intelligence community in its report found that Russian digital interference in global politics could be the “new normal.” With suspected Russian cyberattack campaigns potentially targeting elections in Germany, France, and the Netherlands this year, some Influencers say it’s time to buckle in for the long haul – and focus on defense.
“It was inevitable that traditional espionage would evolve to utilize the Internet,” says Scott Montgomery, vice president and chief technical strategist at Intel Security. “The energy spent on ‘retaliation’ would be better served improving defensive posture and training personnel.”
What do you think? VOTE in the readers’ version of the Passcode Influencers Poll.
Who are the Passcode Influencers? For a full list, check out our interactive masthead here.
Comments:
YES
“While not endorsing direct retaliation, the US should and could do more to protect our networks. Constructive policies include creating legal frameworks that protect the important work done by legitimate security researchers and policies that strengthen and facilitate the use of encryption in the public and private sectors. So let’s talk about how we ‘protect’ against political hacking so we don’t have to ‘retaliate’ against it.” – Abigail Slater, Internet Association
“But only if it is part of a cohesive approach to all nation states. The Russian hacks are important, but should not divert us from the bigger picture. For example, China has waged a largely unanswered cyber offensive against our country that has caused significant economic harm and damaged our national security. In terms of cyber damage, China makes Russia look like amateurs. We need a comprehensive approach, and we needed it yesterday.” – Jenny Durkan, Quinn Emanuel
“And we should not confine our response to the digital domain.” – Influencer
“I caution the US against CyberSaberRattling. Things can escalate very quickly in cyberconflict and spill into physical domains. The US often forgets we are the most connected nation and therefore stand the most to lose. We have too much indefensible [information technology] which can affect free and democratic elections – and even public safety and critical infrastructure. We need to either be ‘less dependent’ and/or ‘more defensible.’” – Joshua Corman, Atlantic Council
“Those who trafficked in US election tampering must be held accountable and dissuaded from considering a repeat offense.” – JJ Thompson, Rook Security
“It needs to be part of a larger coherent strategy that addresses Russia’s broad non-kinetic campaign that includes attacks on the Ukraine and others. They are incrementally executing a high level strategy that is integrated and patient.” – Influencer
“Congress should pass bipartisan sanctions against Russia to inflict additional costs and prevent those costs from being easily reversed by the Trump administration.” – Chris Finan, Manifold Technology
“[The] Obama administration response to the foreign interference in our election can only be characterized as ‘too little, too late.’ The response did nothing to get the Russians to stop the leaks during the election and will do even less in deterring future activities. The President and his team abrogated their responsibility to protect the integrity of the election process.” – Influencer
“Last month’s Russia sanctions and related activities were an important first step, but were only a first step - we’re going to need to do more if we want to deter further Russian interference. In addition to deterrence, this experience should be a catalyst to drive an expanded focus on security solutions not just for large organizations, but also for smaller organizations (like the DNC) that today often cannot afford the type of security that they need.” – Nathaniel Gleicher, Illumio
“First of all, no response encourages further, bolder behavior. Second, remember the U.S. has a full arsenal of options to respond, ranging from hacking back and exposing Botox use all the way through kinetic warfare, with things like sanctions, public shaming, and the like in between.” – Eric Burger, Georgetown University
“We first need better clarity around attribution to the Russian government. There could certainly be classified information from [human intelligence] or other sources that the US government can’t expose, but based on public information, there just isn’t enough to definitively draw a conclusion. If the US government is certain based on other evidence, we need to take a tougher stance. At a minimum, we need to be proactive about locking down our political apparatus to avoid a similar breach, regardless of the actor, in the future.” – Jay Kaplan, Synack
“Materially strengthening existing economic sanctions is in order. Under no circumstances should existing sanctions be lifted.” – Influencer
“But it should have come when the initial sanctions were announced, which came too late after the attribution.” – Adam Segal, Council on Foreign Relations
“And the Intelligence Community should keep it’s [darn] mouth shut about what exactly it is we are doing.” – Influencer
“The Chinese found our sanctions somewhat underwhelming, indicating they don’t have a deterrent effect.” – Dave Aitel, Immunity
“The United States should also have responded earlier in 2016, rather than at the tail end of the Obama Administration.” – Influencer
“Our current lack of deterrence effectively condones the exploitation of computer systems in government and critical private sector enterprises.” – Amit Yoran, Tenable Network Security
“The US should act based on the facts provided from the intelligence.” – Influencer
“The full scope of actions are still unknown, but meddling in our democratic process should not be taken lightly.” – Joel de la Garza, Box
“Tit for tat. There should be a price for their actions, and it should involve doxing powerful Russian’s connected to the Kremlin so they get the point. MAD.” – Influencer
“Our response to Russia’s political hacking has an audience far beyond the walls of the Kremlin. It’s important to signal to other cyber aggressors on the international level that we hold sacred the integrity of our domestic elections at all levels of government.” – Dave Weinstein, State of New Jersey
“US has not, at least publicly, shown enough power and ability in cyberspace operations to act as a deterrent.” – Influencer
“I strongly supported the Obama administration’s response to the information warfare operations targeting faith in the US elections. In particular, the announced actions span a range of domains including diplomatic, economic, and cybersecurity effects. Using a comprehensive approach to counter these unprecedented attacks is a vital step in norm building and puts the world on notice that when they attack US interests in cyberspace, we will respond. That said, I do believe that the actions made public to date are not commensurate with the enormity of the attack on the fundamental underpinnings of our democracy. I will continue to support efforts by the Congress and the new administration to ensure that Russia does not again threaten our electoral systems.” – Rep. Jim Langevin (D) of Rhode Island
“Beginning with voting machines, a thorough audit needs to be conducted, and a time machine needs to be invented to travel back and set up a paper audit trail to verify the results. The US intelligence community has a rare general consensus that Russian hacking of the US election occurred. We need to start by believing them and preparing to create public-facing evidence for the future.” – Influencer
“I am in favor of return fire for any and all. If there is any implication in the question that somehow this episode was the worst, then I reject the question and change my answer. What we are seeing is the weaponization of the data dump and nothing more since, after all, there was nothing fabricated in the DNC e-mails if you want to get down to that level. All in all, the episode means exactly two things: (1) do not put so [darned] much data online and (2) never let data dumps go unpunished even if there is collateral damage in the process or if the perpetrator wraps him or herself in a greater good.” – Dan Geer, In-Q-Tel
“Bullies only back down when they get punched in the nose.” – Influencer
NO
“It was inevitable that traditional espionage would evolve to utilize the internet. The energy spent on ‘retaliation’ would be better served improving defensive posture and training personnel.” – Scott Montgomery, Intel Security
“Based upon the lack of verifiable evidence that can differentiate between state and non-state actors, the US [government] should refrain from any action that could be seen as an escalation.” – Jeffrey Carr, Taia Global
“How can you retaliate against an entity consisting of unwilling victims who unknowingly shuffle attack traffic, launched by a mob of patriotic actors, and directed by a nebulous Russian entity?” – Günter Ollmann, Ablative Security LLC
“Retaliation isn’t a constructive approach, but deterrence is an important capability in any consideration of ways to minimize this sort of activity. We should remember that there were reports of a different foreign nation-state fostering hacks into U.S. political organizations in the 2008-2010 timeframe. We’re not hearing as much noise about those for one reason - the actor didn’t seem to leak their findings. I’m actually less comfortable with that than a case where the actor chooses to at least let us know in a material way some of what they have obtained illicitly. Whether one chooses to view this as an actual new domain for conflict or not, it is not an area in which to operate precipitously or lightly. We have reached a point where proliferation of capabilities is a real concern, and setting an example for measured investigation, attribution, and response is a worthwhile idea.” – Robert Stratton, security entrepreneur, investor, and consultant
“This isn’t as simple as a yes/no question. Should they do more? Perhaps. Are we doing more? Quite likely. Will we or should we know about it? Not necessarily.” – Influencer
“At the end of the day, hacks are going to continue to happen. Organizations will continue to be infiltrated, no matter what the retaliation strategy. Organizations need to arm themselves with the best tools of defense - which secure the network from the inside out, can genuinely self-learn what’s ‘normal’ for a network, and spot anomalies at their nascent stages. While there is no silver bullet to security, it is the only chance we have to stay on top of an ever-evolving threat landscape that is growing in sophistication.” – Influencer