Will your Internet be cut off by DNS Changer Monday? How to find out.
Loading...
Tens of thousands of personal computer users across the US – among more than a quarter-million worldwide – could be caught by surprise Monday when their web browser shows only a blank screen, cut off from the Internet by a federal judge's court order.
The reason behind the cutoff scheduled for 12:01 a.m., Eastern Daylight Time Monday, is a complex tale – a story of Eastern European cybercriminals whose carefully crafted crimeware burrowed into some 4 million personal computers around the globe.
Now, the FBI, which engineered the takedown and is now in charge of the cybergang's US-based network of rogue computer servers, is set to shut them down, even though many victims have not yet cleansed their computers of the malware that hijacks their browsers and sends them to the fraudulent servers.
The FBI managed to get a reprieve in March, arguing that only a fraction of the machines had been fixed. Another reprieve could be granted Monday. If not, estimates suggest that 270,000 to 500,000 machines worldwide – perhaps a quarter of those in the US – had not been cleaned up as of late last month. Some 12 percent of all Fortune 500 companies and 4 percent of “major” US federal agencies still have infected computers, according to Internet Identity, a cybersecurity firm in Tacoma, Wash.
"This is an important moment in Internet enforcement," says Alan Paller, director of research for the Sans Institute, a cybersecurity education organization based in Bethesda, Md. "For the first time I can remember government is involved and is telling citizens to protect themselves."
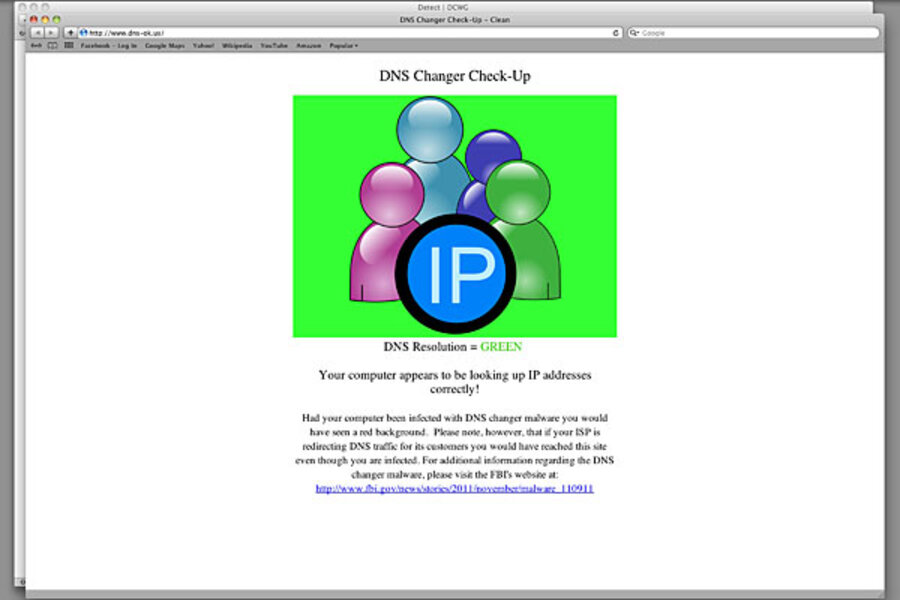
Identifying whether your machine is infected with the DNS Changer malware isn't difficult. Users should click on the DNS Changer Working Group site, then follow instructions. There are also software tools to clean up the problem. But the cleanup isn't a piece of cake, experts say.
One of the things DNS Changer Trojan did beside forcing computers to find the wrong websites on the Internet was to turn off their antivirus updates – and to download to those machines a raft of other malware.
"Unfortunately, most of those that still have infected machines are going to find out the hard way on Monday – they'll be cut off – and have to take their machines to a local computer store to get it cleaned up," says Rod Rasmussen, president of Identity Internet. "The biggest danger for most people isn't going to be the DNS Changer itself, but all the other things that got installed."
DNS Changer, discovered in 2005, was part of a new trend in the malware world designed to subvert one of most basic features of the internet – the addressing system computers use to find websites on the Internet. The rogue servers set up by criminals and later taken over by the FBI in "Operation Ghost Click" were programmed to mimic the Internet phonebook called the Domain Name System (DNS) and transmit their own fraudulent web addresses. In doing so, the criminals essentially enslaved victims' computers, making them dependent on their servers to access the Internet.
The intent of the operation was to twist automated Internet advertising to the criminals' advantage. These advertising systems pay website owners fractions of a cent for every page view and a few cents if someone actually clicks on the advertiser's link. If a sale is made from that click-through, the referring website can actually get a commission.
By sending infected users to fraudulent websites that they controlled, the criminals generated huge numbers of page views and, in turn, large advertising revenues. The money adds up fast when you've got millions of computers under your control pursuing fraudulent search results, says Brett Stone-Gross, senior security researcher at Dell SecureWorks.
"When the user of an infected computer clicked on the domain name link for the official website of Apple-iTunes, the user was instead taken to a website for a business unaffiliated with Apple Inc. that purported to sell Apple software," the FBI reported.
Likewise, someone with an infected computer would click on a link they thought was for the official Internal Revenue Service site, but their browser would instead go to the website for H&R Block, a major tax preparation business – although that company and others were unaware of the scam.
Last November, Estonian authorities scooped up a half dozen suspects believed to have defrauded search-engine companies and online advertisers of at least $14 million.
"The defendants earned millions of dollars under their advertising agreements, not by legitimately displaying advertisements through their Publisher Networks, but rather by using the Malware to fraudulently drive Internet traffic to the websites and ads that would earn them more money," the FBI said in a statement last November.
While the DNS Changer threat seems likely to come to a close Monday, the threat from faked website addressing hasn't gone away and, if anything, is likely to grow in the future. It's already being used in cyberespionage to steal proprietary information, says Mr. Rasmussen of Identity Internet.
"Right now this sophisticated type of attack is still fairly rare," Rasmussen says. "What it's done is to exploit something very basic that changes the way users interact with the Internet. It's particularly dangerous because, at least in theory, the person controlling access to the Internet would be able to see communications. If you route all the traffic through your servers, anything going through these paths is vulnerable."