All Security Culture
- Watch: The Passcode Cup capture the flag competitionPasscode is hosting our inaugural cybersecurity-based capture-the-flag competition, in Washington, D.C. Watch the first and last hours live here on Friday, October 21 at 12:00 and 4:15 Eastern time.
 How America’s first chief information security officer can make his markThe nation’s first ever chief information security officer (CISO) has a big task — and can make a big impact.
How America’s first chief information security officer can make his markThe nation’s first ever chief information security officer (CISO) has a big task — and can make a big impact. Hackers for good: How Anand Prakash rescued FacebookIn the first installment in an occasional series about ethical hackers, Passcode profiles one of India's most successful freelance cybersecurity researchers known for finding – and helping fix – serious flaws in Facebook.
Hackers for good: How Anand Prakash rescued FacebookIn the first installment in an occasional series about ethical hackers, Passcode profiles one of India's most successful freelance cybersecurity researchers known for finding – and helping fix – serious flaws in Facebook. How to pick a password managerAfter the Yahoo breach exposed personal data about 500 million users, many people are looking for ways to protect themselves online. That's where password managers come in.
How to pick a password managerAfter the Yahoo breach exposed personal data about 500 million users, many people are looking for ways to protect themselves online. That's where password managers come in. Digital attack on journalist raises specter of online censorshipAfter an unprecedented online assault took down cybersecurity journalist Brian Krebs's influential cybersecurity blog, he was able to return to the web because of a new service that protects journalists and activists from online censorship.
Digital attack on journalist raises specter of online censorshipAfter an unprecedented online assault took down cybersecurity journalist Brian Krebs's influential cybersecurity blog, he was able to return to the web because of a new service that protects journalists and activists from online censorship. The best way to learn about computers: break themTravis Goodspeed, an independent cybersecurity researcher, says tinkering leads to better cybersecurity.
The best way to learn about computers: break themTravis Goodspeed, an independent cybersecurity researcher, says tinkering leads to better cybersecurity. What cybersecurity leaders say we can do now to advance the cybersecurity workforceThe cybersecurity talent shortage is no secret. Here are ways experts are working to fix it.
What cybersecurity leaders say we can do now to advance the cybersecurity workforceThe cybersecurity talent shortage is no secret. Here are ways experts are working to fix it. When Alexa is listening, what do you tell houseguests?If you've plugged in an eavesdropping personal assistants such as the Amazon Echo Dot, are you obligated to warn visitors, 'Be careful what you say, Alexa is listening'?
When Alexa is listening, what do you tell houseguests?If you've plugged in an eavesdropping personal assistants such as the Amazon Echo Dot, are you obligated to warn visitors, 'Be careful what you say, Alexa is listening'? Take it from a parent, ask your kids before you post to FacebookTalking to kids about digital security and privacy is critical. But parents need to set examples, too, and that may mean considering their own kids' privacy before posting every moment of their lives online.
Take it from a parent, ask your kids before you post to FacebookTalking to kids about digital security and privacy is critical. But parents need to set examples, too, and that may mean considering their own kids' privacy before posting every moment of their lives online. What Teddy Roosevelt can teach us about cybersecurityWhy wait years to grow new cybersecurity talent when you can take advantage of the talented federal workforce today?
What Teddy Roosevelt can teach us about cybersecurityWhy wait years to grow new cybersecurity talent when you can take advantage of the talented federal workforce today? Opinion: Cracking the cybersecurity gender codeAttracting more women into the male-dominated cybersecurity field means ditching the bro pipeline of computer science, military, and intelligence recruits and drawing from disciplines such as law and public policy.
Opinion: Cracking the cybersecurity gender codeAttracting more women into the male-dominated cybersecurity field means ditching the bro pipeline of computer science, military, and intelligence recruits and drawing from disciplines such as law and public policy. Why hackers are so obsessed with picking locksIt's the physical manifestation of what they often try and accomplish in the digital world, say lock-picking enthusiasts.
Why hackers are so obsessed with picking locksIt's the physical manifestation of what they often try and accomplish in the digital world, say lock-picking enthusiasts.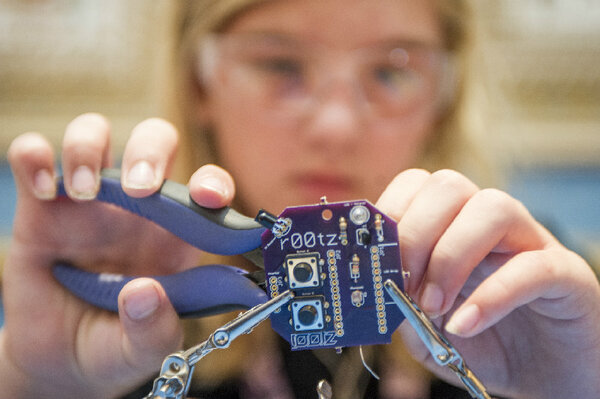 Video: So you want to be a hacker? Advice from the kids of DEF CONPasscode caught up with some of the kids at r00tz Asylum to get their advice: What's the first step other kids – or anyone, really – should take if they want to be a hacker?
Video: So you want to be a hacker? Advice from the kids of DEF CONPasscode caught up with some of the kids at r00tz Asylum to get their advice: What's the first step other kids – or anyone, really – should take if they want to be a hacker? Obama plan to boost cybersecurity workforce fails to impress professionalsCybersecurity experts say a White House plan to bolster numbers of professionals working to safeguard federal networks doesn't go far enough.
Obama plan to boost cybersecurity workforce fails to impress professionalsCybersecurity experts say a White House plan to bolster numbers of professionals working to safeguard federal networks doesn't go far enough. With the drama but not the bruises, hacking becomes a spectator sportDARPA staged the world's first live computer-versus-computer hacking competition in which teams battled for a multimillion dollar purse in front of thousands of cheering fans in Las Vegas.
With the drama but not the bruises, hacking becomes a spectator sportDARPA staged the world's first live computer-versus-computer hacking competition in which teams battled for a multimillion dollar purse in front of thousands of cheering fans in Las Vegas. Hackers grapple with a once-unthinkable idea: Political actionAs the DNC hack puts digital security in the national spotlight, cybersecurity professionals took the unusual step of staging a Hillary Clinton fundraiser at a hacker conference known for its fiercely independent and antiestablishment attendees.
Hackers grapple with a once-unthinkable idea: Political actionAs the DNC hack puts digital security in the national spotlight, cybersecurity professionals took the unusual step of staging a Hillary Clinton fundraiser at a hacker conference known for its fiercely independent and antiestablishment attendees. Opinion: The value of talking to girls about technologyTo boost the number of women in technology, first we need to treat girls interested in tech as normal, and stop forcing them to make a false choice between girliness and geekdom.
Opinion: The value of talking to girls about technologyTo boost the number of women in technology, first we need to treat girls interested in tech as normal, and stop forcing them to make a false choice between girliness and geekdom.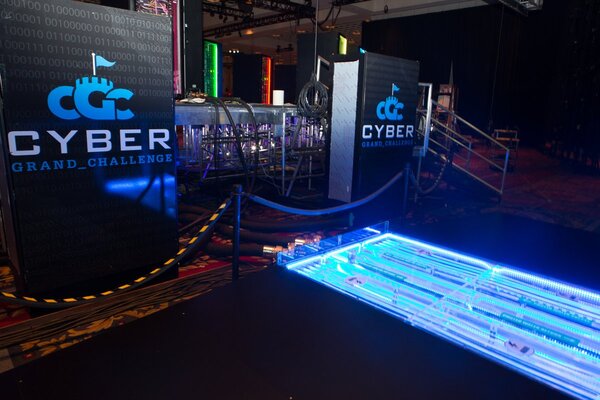 High-stakes DARPA hacking contest pits computer against computerThe Pentagon's research wing this week will stage an unprecedented digital battle in Las Vegas in which machines will attempt to autonomously find and fix computer security flaws.
High-stakes DARPA hacking contest pits computer against computerThe Pentagon's research wing this week will stage an unprecedented digital battle in Las Vegas in which machines will attempt to autonomously find and fix computer security flaws. Machines v. hackers: Cybersecurity's artificial intelligence futureThe US is short hundreds of thousands of information security professionals. But that gap is driving investments in artificial intelligence that may make armies of cybersecurity workers unnecessary.
Machines v. hackers: Cybersecurity's artificial intelligence futureThe US is short hundreds of thousands of information security professionals. But that gap is driving investments in artificial intelligence that may make armies of cybersecurity workers unnecessary. Opinion: How to talk digital privacy with kidsIt may not be possible without eliciting moans and eye rolls. But the digital privacy talk is essential in an era when technology is so intimately intertwined with childhood.
Opinion: How to talk digital privacy with kidsIt may not be possible without eliciting moans and eye rolls. But the digital privacy talk is essential in an era when technology is so intimately intertwined with childhood.






















