Child porn on government devices: A hidden security threat
Loading...
Daniel Payne, director of the Pentagon's Defense Security Service, admitted this spring to encountering “unbelievable” amounts of child pornography on government computers.
The comment came during an event in Virginia where military and intelligence officials gathered to address threats posed by federal workers. Mr. Payne, who spent much of his career in senior CIA and intelligence community roles before taking the Pentagon post, wanted to stress the value of monitoring employees' systems to ensure they remained fit to handle top-secret information.
But the revelation raised many more troubling questions. Who was downloading the sexually explicit and criminal material? How much of it was on intelligence agency networks? And why didn't the federal government deploy more robust technologies to keep child pornography from spreading on its networks?
While the notion of government employees and contractors with high levels of security clearance looking at child pornography was disturbing on its own, internal records retrieved through the Freedom of Information Act revealed the problem is not limited to military and intelligence agencies.
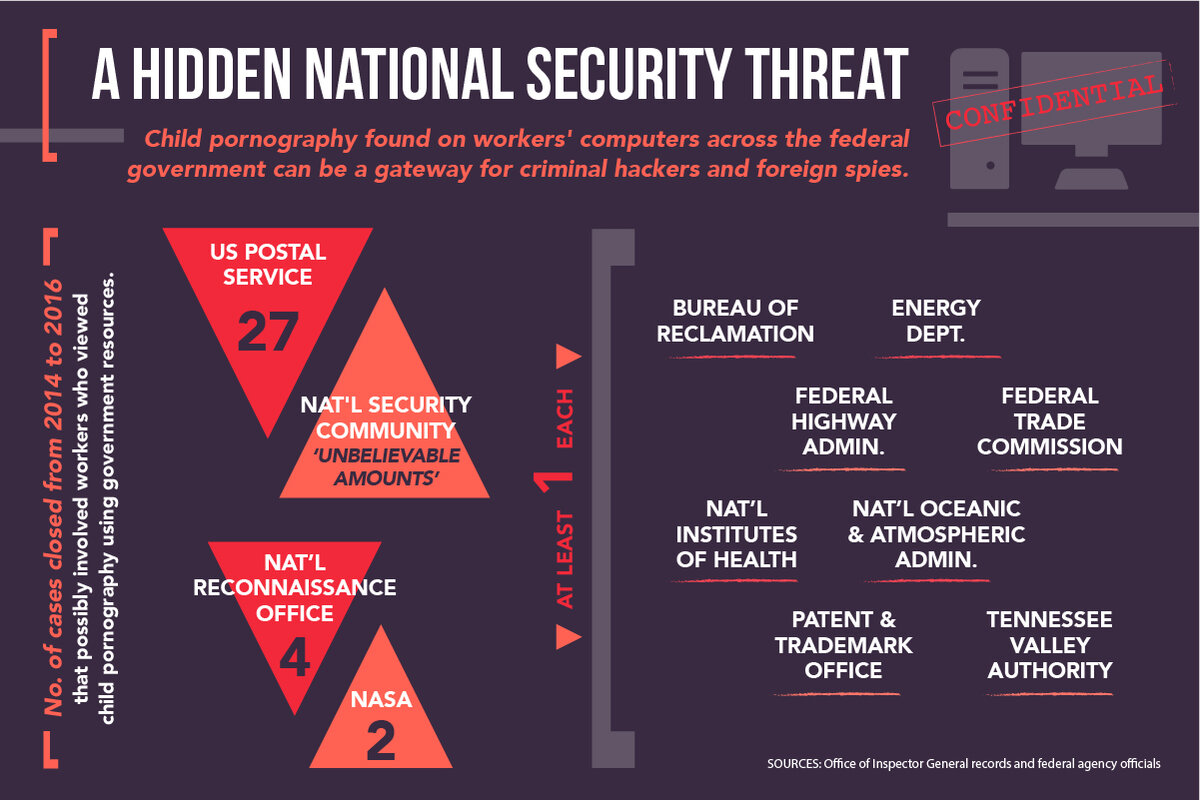
In the past three years, agencies ranging from the Postal Service to the Federal Highway Administration substantiated about 40 allegations that employees or contractors opened child pornography or provocative images of minors using government resources. The number of confirmed cases may be higher now since many federal organizations, such as the National Security Agency (NSA), did not respond to requests for records about similar investigations.
At a time when the US government is struggling to contain the problem of insider threats – employees who, for instance, steal national secrets or unwittingly damage US security by infecting federal computers systems with malicious software – pornographic images of children on government computers present a profound national security risk that if left unresolved could endanger American lives at home and abroad.
In interviews with more than a dozen federal officials and cybersecurity experts, they all acknowledge that government employees who download child pornography are more susceptible to coercion by foreign spies and criminal hackers.
What’s more, the forums where pornographers trade in sexual images of children are rife with malicious software, giving criminal hackers or intelligence operatives working with America’s adversaries myriad ways to infiltrate US government computer networks to potentially steal state secrets.
“These people misusing their computers, their government property, in addition to being odious and really stupid, does create an additional risk because they are subject to blackmail and the like,” says Larry Clinton, president of the Internet Security Alliance, a tech industry group. “And we have a major problem with the insider threats of cybersecurity, including people who are compromised for various reasons.”
Indeed, foreign attackers often initiate cyberespionage campaigns by breaking through the point of least resistance on a network – such as careless employees. For instance, the alleged Russian hackers who infiltrated US political parties ahead of the presidential election exploited human security weaknesses to tamper with the election, baiting political operatives to click bogus security alerts that offered cyber spies entree to email accounts.
Criminal hackers commonly use ads and other images on porn sites to deliver malicious software designed to steal passwords, infect computers, and encrypt documents on victims’ computers. A May 2015 study by the cybersecurity firm Blue Coat Systems found that pornography, in general, continues to be one of the most popular methods that hackers use to hide malicious software. The spring of that year, security researchers discovered that hackers installed programs designed to infect users’ computers in highly popular porn sites that accounted for more than 250,000 million monthly visits.
And it’s not just criminal hackers that are delivering malware through sites where people trade in pornographic images. Last month, tech reporter Joseph Cox reported in Motherboard that the FBI took advantage of a “nonpublicly known vulnerability” to unmask users of a child pornography site called Playpen, which is accessible only through the anonymizing web browser Tor.
The case illustrates how government agencies can track people on supposedly hidden forums that trade in illicit images. "A lot of these types of sites are accessible through Tor browsers," said Steve Bongardt, a former profiler with the FBI's cyber behavioral analysis program. "They are not absolutely anonymous," he added, pointing to the Playpen investigation.
So while those who traffic in child pornography face a federal 30-year maximum prison sentence for a first-time offense, those who are government employees – especially the ones stashing images on government computers – bring even higher national security risks.
"The risk of a foreign intelligence service using a federal employee's child pornography habit, particularly online, in the last two decades, and trying to coerce that individual into recruitment is well known, and an accurate high threat," said Mr. Bongardt, who now works as a private insider threat and computer forensics analyst as president of consulting firm the Gyges Group.
“If a foreign government takes a hard look at recruiting someone, they have the ability to find out a lot about their online behavior and in the context of that, there have been cases, where they then use that behavior to leverage a recruitment against that individual,” he said, speaking about deviant personnel in general, not child pornography users specifically.
Inspector general officials within the Tennessee Valley Authority, a government-owned utility, and NASA, as well as other agencies, said flat out that they feel digital child pornography could jeopardize government networks.
"Yes, because the systems that those images are kept on are notorious for malware and other illegal activities that could infect agency computers, thereby putting agency information at risk," says Stefanie Hoglund, spokeswoman for the Tennessee Valley Authority Inspector General.
Additionally, says Renee N. Juhans, inspector general executive officer for NASA, employees who have visited child porn sites or downloaded explicit content are far less likely to report problems with their work computers, leaving them far more exposed to criminal hackers and spy operatives.
The threats inside
Shaken by recent internal security lapses in general, the Obama administration is in the midst of overhauling screening procedures for national security employees and contractors. Information leaks by ex-NSA contractor Edward Snowden and the fatal shooting of 12 people in the Washington Navy Yard by a contractor shaped the reforms, along with a massive hack of background check records at the Office of Personnel Management (OPM) that was discovered in 2015. More recently, the NSA began investigating perhaps the biggest ever leak of top-secret documents allegedly at the hands of agency contractor Harold Thomas Martin who was arrested this summer.
The new personnel vetting approach will include automatic checks of social media, criminal records, and other data sources. The aim is to continuously evaluate a person's behavior for signs the individual may constitute a security threat. A new information hub to help flag potential threats will share data from “user activity monitoring” of employees’ computer activities, according to a May 19 Privacy Act notice. Network surveillance may record keystrokes, screenshots, and content transmitted via email, chat, and data import or export.
According to OPM, some measures are currently in place to spot child pornography users within the federal workforce. "Background investigations do rely on the cooperation of individuals and the accessibility of records," an OPM spokeswoman said in an emailed statement. “Background investigations have processes designed to obtain information about adverse conduct such as this through reviews of records, interviews and searches of relevant data sources.”
The Obama administration doesn’t keep official numbers related to employees who access child pornography on federal government computers. The government's basic firewall does not have the capability to recognize child porn, according to the Homeland Security Department (DHS). That system, called EINSTEIN, helps detect and thwart known cyberassaults, while another antimalware program called Continuous Diagnostics and Mitigation, comprising an array of sensors and services, flags network risks. The two DHS-led efforts "do not investigate the behavior of individual employees," a Homeland Security official said.
Last week, a White House commission released cybersecurity recommendations for the incoming Trump administration and called post-Snowden efforts to address the insider threat problem "at best uneven and far too slow." The panel, whose members included former NSA Director Keith Alexander, said the next administration should make adequate funding available and direct a deputy assistant to the president to oversee that problem.
An annual defense policy package that Congress could pass as early as this week orders the Pentagon by Sept. 30, 2019, to finish crafting a tool that collects and stores "user activity monitoring" records plus other personnel data on federal workers. The bill also authorizes $5 million for developing insider threat systems.
Scope of the problem
It's unclear if federal investigators uncovered malware on computers or thumb drives they searched in the dozens of cases where they uncovered child porn. The probes focused on employee wrongdoing, not cybersecurity. Agency inspector general offices referred most allegations they could corroborate to the Justice Department for potential prosecution.
This year alone, for instance, the Postal Service has completed nine investigations into alleged access of child pornography on government computers, according to inspector general records obtained through a Freedom of Information Act request. Between 2014 and 2016, the USPS inspector general closed 34 investigations into that category of misconduct. At the same time, the Postal Service has more than a century of experience identifying people who traffic in the illicit market, because offenders used to distribute child pornography via snail mail.
"If anyone is probably reporting and very sensitive to it, it’s going to be them," said Bongardt, the former FBI agent. "They are very good about trying to police their own, with regards to it.”
Postal Service investigators substantiated 79 percent of the 34 cases, said Bruce Marsh, USPS inspector general director of government relations. "A few of the substantiated allegations involved employees found to have involvement with child exploitation/pornography but not on postal systems," he said.
One well-known case of a government employee charged in connection to child pornography is that of Federal Highway Administration staffer Eric Worrell. According to a March 2016 Inspector General report from the Transportation Department, Mr. Worrell's alleged transgressions came to light when a personal thumb drive of his containing child pornography was found in a hallway in a Sacramento, Calif., federal building.
The department’s investigation "identified hundreds of images of child erotica and child pornography" on Worrell’s government-issued computer, according to the report. "He was taken into custody and the federal computer that he used there at the office was seized as part of the investigation to determine whether any of that material was on a government computer," Federal Highway Administration spokesman Doug Hecox said. Worrell left the agency in March 2015. The US Attorney's Office for the Eastern District of California announced this March that US District Judge Troy L. Nunley sentenced Worrell to five years in prison, followed by 20 years of supervised release.
At least a handful of people who once had clearance to log into military and intelligence networks allegedly viewed child pornography or child erotica at various times during or before 2009 – and as recently as 2014, according to one spy agency. The National Reconnaissance Office (NRO) cut off four individuals' access to the spy satellite agency's systems and information, or denied them access if the individual was undergoing a security investigation, after probing their activities, agency officials said. The NRO referred the cases to Justice.
A 2014 NRO investigation reported that a software engineer contractor "made admissions of 'cracking' secure wireless networks and viewing child pornography on the internet." The subject had been granted access to sensitive NRO networks on June 25, 2012 and denied access in November 2013. The wireless network the contractor claimed to have hacked was not an agency network, an NRO official said.
A separate 2014 probe claimed another person associated with the agency admittedly "viewed, downloaded and saved child pornography" about 30 times within two months in 2009. That individual had access to NRO classified information between 2009 and 2013 but there’s no evidence that person used NRO computer systems to access child pornography, the agency said. The material involved in that case consisted of pornographic images of 15 to 17 year old females.
"Substantiated cases of child pornography result in termination of employment at the NRO and the revocation of access to classified information," agency spokeswoman Loretta DeSio said.
At NASA, a search of an employee's department-issued flash drive revealed 122 images of two prepubescent girls, about 8 to 12 years old. The pictures showed the girls "provocatively posed in bikinis, short skirts, shorts, and/or high heels," according to a November 2015 inspector general report. Also, a bag holding the employee's work-issued Dell laptop stowed a personal hard drive allegedly containing "thousands of images of young girls in provocative poses in addition to two images which appear to be child pornography," the report states. "All available evidence was presented to prosecutors," NASA spokeswoman Karen Northon said in an Aug. 9 email, adding, "the subject is no longer a federal employee."
Limits to tracking child porn
Another reason the federal government does not track the number of child pornography users among its ranks is because the FBI says “a child pornography offender’s place of employment is not relevant to their sexual interest in children," says Matthew Bertron, an agency spokesman.
"Child pornography offenders typically use multiple devices and media to engage in the possession, distribution and/or production of child pornography; so it is not surprising if such activity also occurred with government provided devices/networks and while at work. In fact, it underscores this need-driven behavior and how their desire to access this illegal material outweighs the risk of getting caught at work or while using a work device," said Mr. Bertron. "The FBI is focused on eliminating child pornography and arresting any offender no matter where they are or who they work for."
But many experts say the offender’s employer does matter when attackers are attempting to target high-level government officials. If you are cyber spy, "a lot of times you don’t care about the third level admin who’s bored and is looking at whatever they are looking at -- but you are using that as a pathway to get to the person the admin works for who may be really important and have important information on his or her system," said Mr. Clinton of the Internet Security Alliance.
Network monitoring systems and background checks are supposed to catch unauthorized internet viewing, but due to inadequate personnel investigations, policy issues, and funding constraints, not every department has the ability to prevent IT abuse, security experts say. Some but not all agencies use programs for filtering specific web content on employee devices.
"Government, as well known at this stage, has often not invested adequately to protect their own systems," said Clinton. "Historically, the agencies have not adequately received funding for cybersecurity writ large." In fiscal 2014 and again in fiscal 2015, agencies collectively spent about $13 billion on data protection, according to White House reports on compliance with federal information security legislation. For fiscal 2017, Obama has requested $19 billion from Congress for cybersecurity, a 35 percent boost over the sum lawmakers approved for fiscal 2016.
Tech problems and human solutions
One of the agencies equipped with web-tracking tools is the Federal Trade Commission, where officials made a point of noting that the agency's security system immediately alerted officials when software detected potentially illegal images. The FTC's web filter, developed by Blue Coat, indicated a male employee attempted to open two websites that the filter categorized as containing "child pornography," according to a May 2015 inspector general report. The FTC IG was notified that same day. Later, separate monitoring software installed on the employee's machine determined he accessed or at least tried to access several images "of young, post-pubescent nude Asian girls posing in lascivious positions," the report states.
The Commerce Department also has been using "protective filtering tools" to detect – and block – downloads of unlawful pornography by employees, department officials said in an emailed statement, adding that "all requests are logged, analyzed and reported" to the inspector general.
One of several allegations that Commerce probed involved an employee in the National Marine Fisheries Service's Southeast Regional Office who attempted to download images an agency firewall tagged "as being of a child pornographic nature," an October 2014 investigation states.
To outwit monitoring systems, federal employees who traffic in child pornography have resorted to encrypting their communications to avoid detection, according to experts. And while government managers have the authority to shut down encrypted channels on agency networks – doing so could have adverse effects and also lead to malware infections on government networks.
"What if someone wants to do online banking? And almost every type of website that you go to now has some type of HTTPS," an increasingly popular setting that prevents hackers from intercepting what you submit on a site, said Bongardt, the ex-FBI profiler.
Some organizations could end up embracing decryption tools with the sophistication to only peer into dangerous content and leave private correspondence alone. These systems search emails for strings of letters or words such as "intellectual property," "classified," or "confidential," to prevent leaks and other abuses, without reading and saving personal messages, he said. "We’ve got to have the ability to really look at that and make sure we know all the data that’s going on and traversing our networks and that’s really important,” he said.
In addition to a technical solution, Bongardt said, there’s also an important human element to catching and trying to eliminate child pornography from federal workers’ computers. "We don’t want everybody being paranoid about looking at their neighbor,” he said. “But if they happened to see, looking over John’s shoulder, something on their box that looks like child pornography, we have to train our people and give them the ability to report that.”